
12 Aug Universal ZTNA from Extreme Networks
In today’s digital world, cybersecurity is an absolute top priority for companies of all sizes. With the advent of the NIS2 directive, cybersecurity requirements are becoming even more stringent. One of the biggest challenges for organizations is providing secure access to corporate systems, both for office and remote workers. Extreme Networks offers the ideal solution with their Universal ZTNA (UZTNA). In this blog post, we discuss this solution from Extreme Networks in more detail.
The challenges
The advent of the NIS2 directive is very important. This legislation sets the outlines within which companies must operate to comply with cybersecurity measures imposed by governments. This presents a major challenge for network and security engineers, who must set up IT environments so that everyone within the organization can be securely and efficiently connected to the necessary applications, whether they are running on-premises or in the cloud. Within this connectivity component, you are faced with two challenges.
Within the domain of connectivity, there are two main challenges:
- Secure connection in the office or on-site: How do I ensure that my users who are on-site are securely authenticated and connect to the network?
- Secure remote connection: How do I ensure that my users, regardless of their location (at home, at clients, at a coffee shop, etc.), can securely connect to the required applications?
Solutions such as Network Access Control (NAC) and Zero Trust Network Access (ZTNA) already exist for these challenges. However, the problem is that these are often separate products, with no ability to implement a unified policy that solves both challenges and can be managed from one central point.
Universal Zero Trust Network Access (Universal ZTNA)
Universal Zero Trust Network Access or Universal ZTNA ensures that 1 policy is introduced for users regardless of where they are located.
However, this is a term that is viewed differently by quite a few vendors. Some vendors adopt the principle that users, regardless of their location, connect via a client to a central point (full-tunnel), with all network traffic being routed through that tunnel. Centrally, the traffic is inspected and processed according to a set of policies, then routed to the appropriate network (IPSec, SaaS, etc.). Other vendors, including Extreme Networks, combine a Cloud NAC solution for the campus with ZTNA for remote workers.
Extreme Networks recently added Universal ZTNA to its portfolio. This solution combines Cloud NAC for the campus with ZTNA for remote workers. Below in more detail how the different solutions fit together and exactly what the unified policy looks like.
Cloud NAC
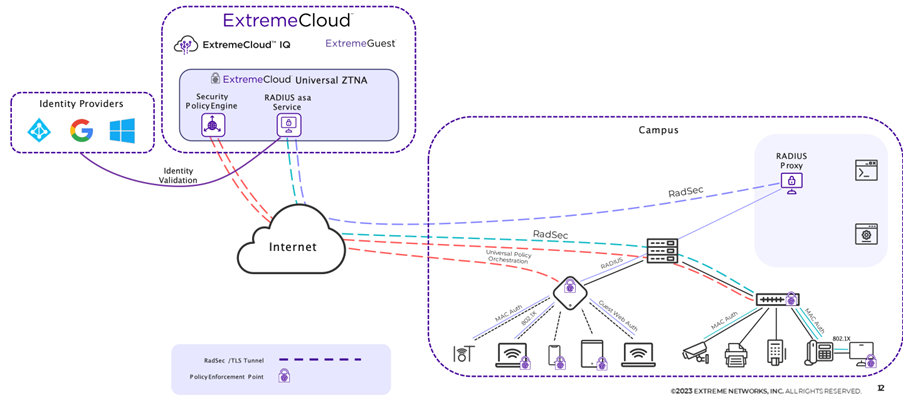
The diagram above shows how the Cloud NAC works correctly and what components are present.
Within the Cloud NAC, there are several components:
- Identity Providers: An Identity Provider is needed to import the users that will use the UZTNA solution. Within Cloud NAC, these are used as the backend authentication server for 802.1X Radius. A user connecting to the network (whether wireless or wired) is authenticated via the Radius service against the credentials known within the Identity Provider (Entra ID, Google Workspace, Onprem AD).
- ExtremeCloud: Within ExtremeCloud, you have two applications:
- ExtremeCloud IQ: The SaaS Network Management solution from Extreme Networks in which switches and access points are managed. For this solution, within ExtremeCloud IQ, you configure the link between LAN/WLAN and the UZTNA Cloud NAC
- ExtremeCloud Universal ZTNA: This is the UZTNA application in which you will configure all policies, rules, ….
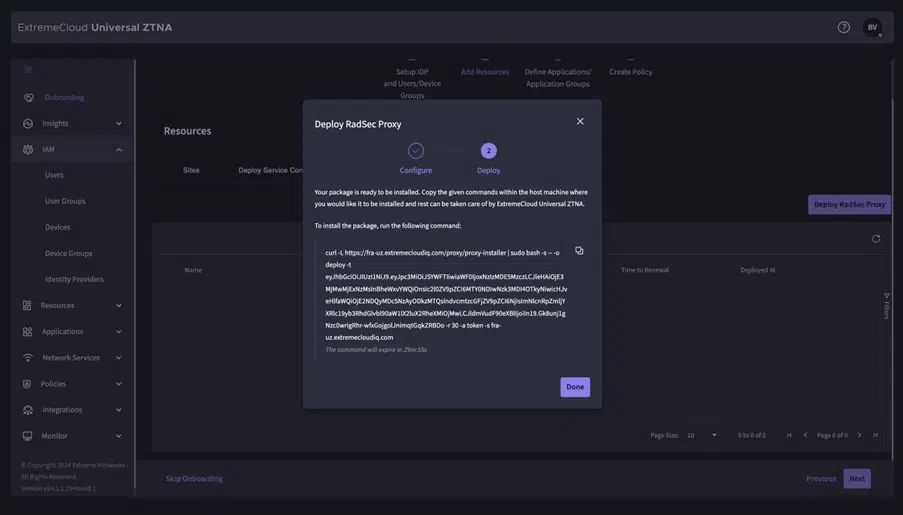
- Campus: Within the campus, the switches and APs run, which create a RADSEC tunnel to ExtremeCloud which then processes the authentication and sends back a response. There are switches and APs that send RADSEC directly to ExtremeCloud, older switches and later 3rd party switches first send Radius to a Radius Proxy that is local, which in turn sends RADSEC to ExtremeCloud.
RadSec is the abbreviation for “Radius Security.” This is a protocol used to secure RADIUS (Remote Authentication Dial-In User Service) communications by providing additional encryption.
RADIUS is widely used in network environments for authenticating and authorizing users before allowing them onto the network. Mainly for wireless applications (as we also authenticate with the KappaData wifi), but also for wired applications (with a network cable to a switch). In addition, it is also often used to provide authentication on VPN applications, for example.
The standard RADIUS that is not encrypted sends data in plain text, making it vulnerable to various attacks such as man-in-the-middle attacks or replay-attacks. By using TLS (which is also used for HTTPS Web traffic), RADIUS messages are encrypted and are better protected against attacks.
UZTNA – Application access
The second component within UZTNA is application access. With this you give remote workers access to applications, wherever they are located.
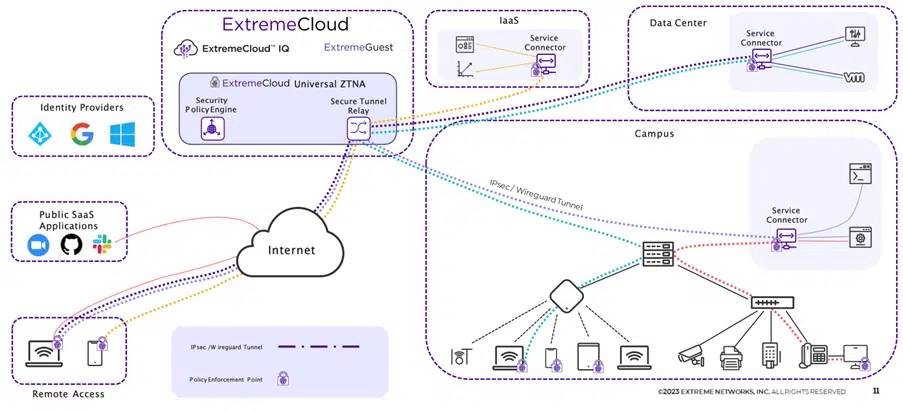
Even within Application access, you have different parts:
- Identity Provider: This is the same Identity provider as discussed within Cloud NAC. The Identity Provider contains groups that you can use in policies to make certain applications available to a group of users.
- Public SaaS Applications: These are applications where you can configure that they can only be used via a UZTNA connection. If a user connects via UZTNA they can use the application, if they do not have a connection to UZTNA they will be Rejected. At the time of writing these are: Mulesoft, Salesforce, Slack, G Suite, Splunk, Github, Atlassian, Dropbox and Zoom.
- Remote Access: This is a user who has the UZTNA Agent on their device that they connect to towards ExtremeCloud. This is agent based or possibly agentless as well.
- ExtremeCloud: This is the Universal ZTNA application where the policies are defined. The Secure Tunnel Relay ensures that the connections coming in through the agents are sent to the right applications.
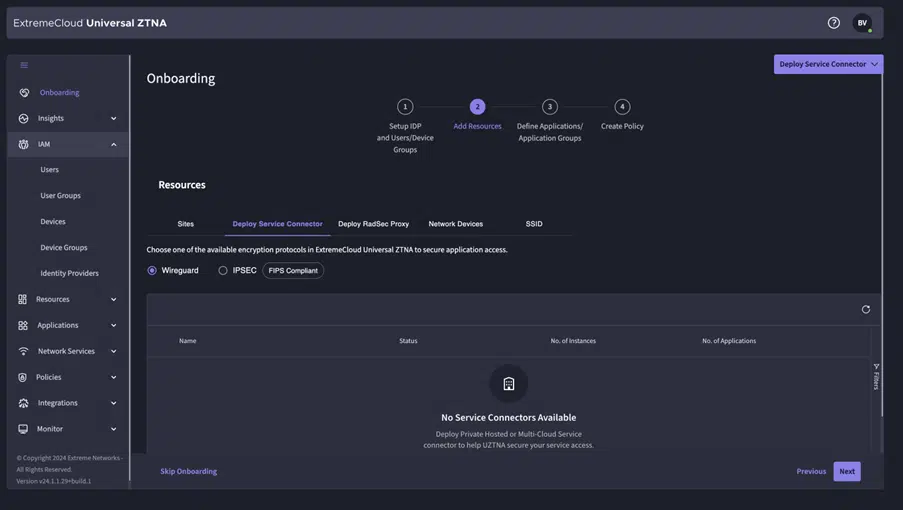
- IaaS (Infrastructure as a Service): Applications running in the Public Cloud (AWS, Azure, Google Cloud).
- Data Center: Applications running in a Private Data Center (a service connector is installed on the hypervisor)
- Campus: Applications running on campus (a service connector is installed in the campus network)
Policies
In the previous sections, we discussed connectivity. Of course, the most important thing about a ZTNA solution is defining Policies. Below, we will discuss step by step how to set up Universal ZTNA from Extreme Networks:
Extreme Universal ZTNA Flow
Step 1:

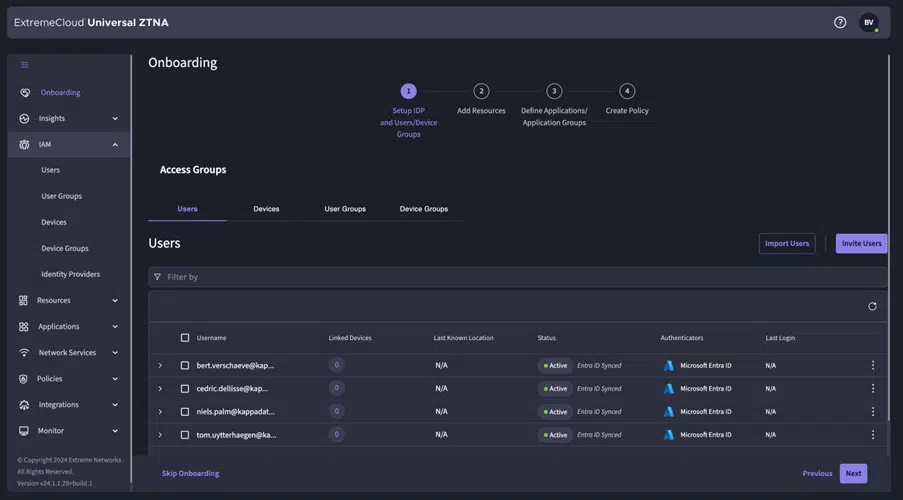
Homescreen
When we log into ExtremeCloud Universal ZTNA, we see a general screen that gives us insights into what is currently going on. Here you can see the health status of the applications, service connectors and Radsec proxies, along with the general usage of the applications made available through Universal ZTNA.
Integration Entra ID
Next we get the screen to set up the integration with Entra ID. We create an App registration within Entra ID and configure it with the appropriate values so that there is a connection between Entra ID and ExtremeCloud UZTNA.Because Cloud NAC cannot support MFA, we need to create a Conditional Access rule within Entra ID that bypasses MFA for that particular application.
Then you can set up a SCIM sync by creating an Enterprise Application in Entra ID so that all groups and users are automatically synced between UZTNA and Entra ID.
Step 2:
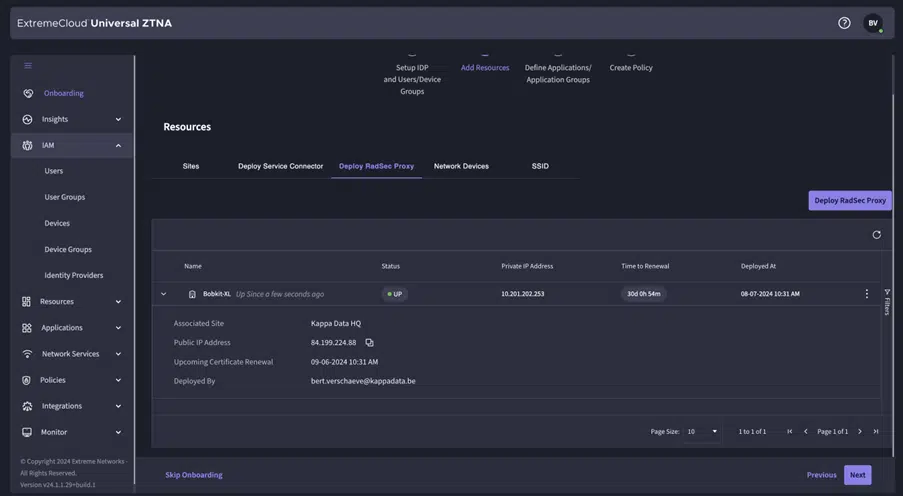
CloudNAC & UZTNA Connection
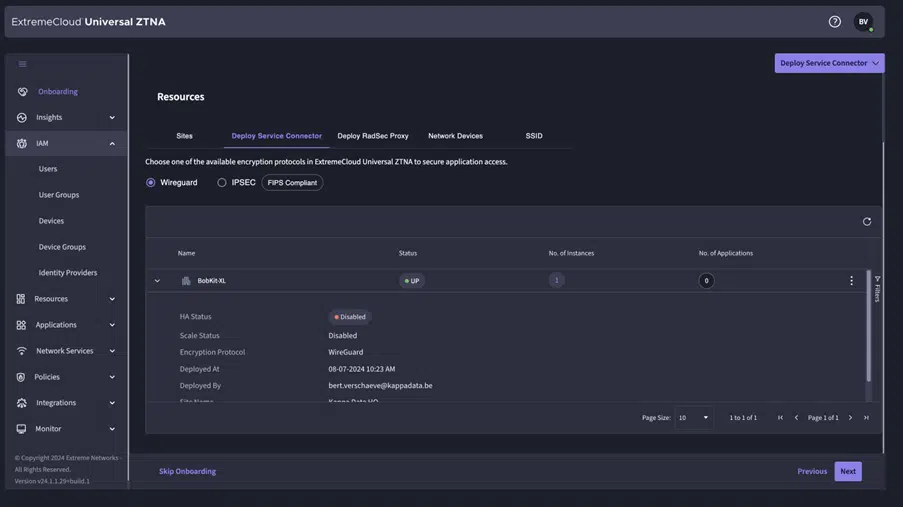
Within the devices, we see the APs and/or switches that are currently eligible to communicate with the Cloud NAC. This is also a sync between ExtremeCloud IQ and UZTNA. Currently, the APs are still communicating with a Radsec proxy, and so the SSID is configured with the Radsec proxy as the Radius server.Step 3:
Step 4:

Definition Hybrid Policy
Now it is time to start defining a hybrid policy. We will now create this one specifically for the Solution Engineers group.In it you define a number of things
- Name of the policy
- User group
- Device group
- Application group
- Network (VLAN or Fabric I-SID)
- Network resource group (certain IP/subnet/port combinations to be blocked)
Conditions
There is also a form of Conditional Access for Cloud NAC built into UZTNA. That way, access can be denied/allowed based on:
- Location
- Time
- Authentication (EAP-TLS, EAP-TTLS, MBA,…)
Device Posture
Access to applications can be denied if the agent notices that a number of things are out of order.

MDM
There is also an integration with Microsoft Intune so you can give only compliant devices access through UZTNA

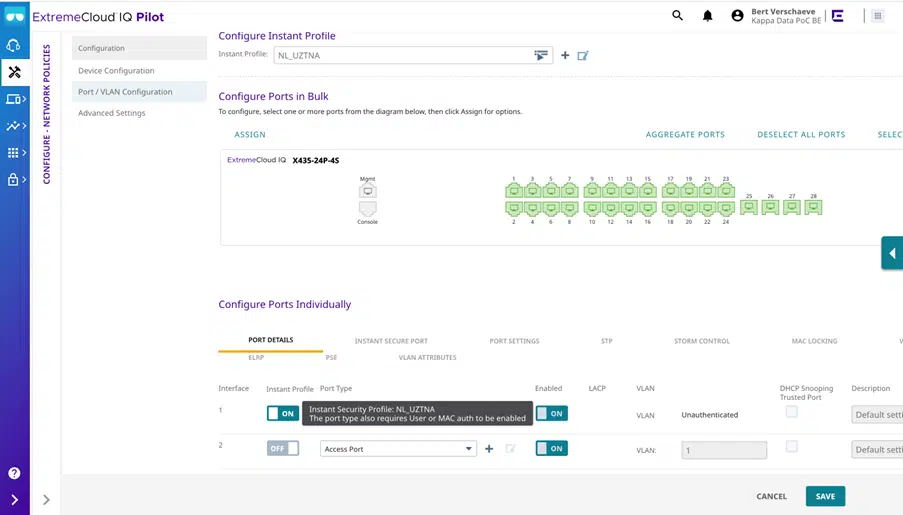
Switch Configuration
Within ExtremeCloud IQ, you can select the “Instant Secure Port” to make the switch port a “NAC” port. This way, Radius requests on that port are forwarded to UZTNA.

Wondering how Universal ZTNA from Extreme Networks can help your organization meet the more stringent requirements of the NIS2 directive while providing secure access to your employees?
Please feel free to contact [email protected] if you would like more information.

















No Comments