
08 Mar Understand your enemies: 4 phishing statistics to help you defend yourself
Cybersecurity is constantly evolving. That’s why we, along with Whalebone, are showcasing some data that can help you in your efforts to protect your company’s network from attackers. In this blog post, we take a closer look at phishing, an increasingly popular method of tricking people into releasing data, downloading malware or otherwise compromising their company’s security.
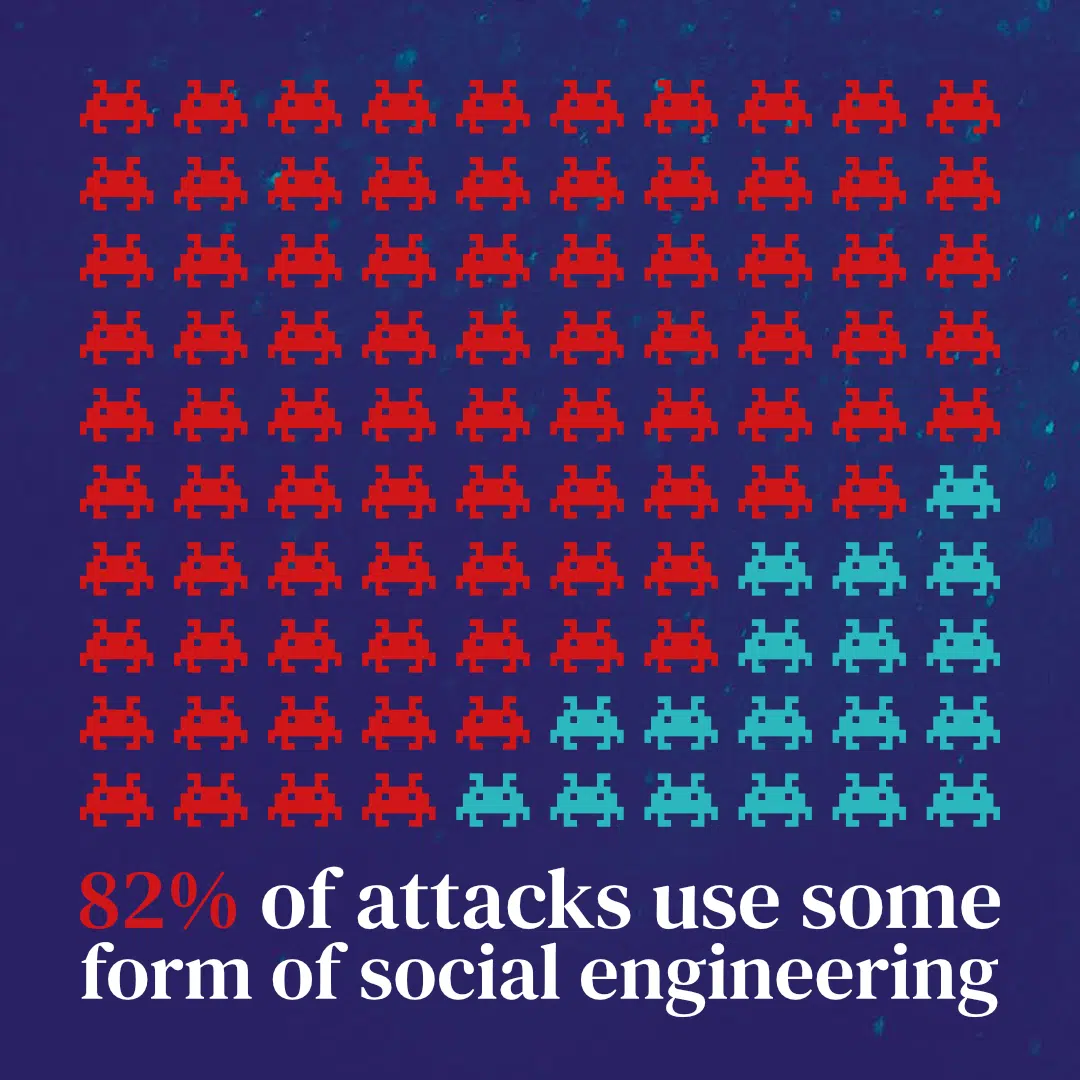
Human factor remains weakest link within cybersecurity perimeter
Verizon’s 2022 DBIR reveals that 82% of data breaches have a human component, including phishing and the unauthorized use of stolen credentials. This underscores how important it is for organizations to implement robust authentication measures, such as multifactor authentication, to prevent unauthorized access to sensitive information. Frequency of social engineering-based attacks DNS protection has the advantage of examining the domain itself and not just device activity or traffic.
In addition, Immunity assesses domains based on extensive data from various external sources, internal research and insights from our customers in telecommunications, Internet service provider (ISP) and business. As a result, Immunity can even identify threats that are not yet included in a threat intelligence database.
Mimicking authority figures remains the preferred method for phishing attempts
KnowBe4 reveals global ranking of topics for phishing emails, including emails impersonating Google Docs, HR policy updates and IT reports. This highlights the importance of educating and raising user awareness to recognize phishing attacks and avoid becoming a victim. In 8 of the top 10 subject lines, attackers pose as authority figures about the employee or their accounts.
The most common subject lines
However, emails are constantly evolving, and with the advent of new AI capabilities, it will become increasingly difficult to distinguish genuine emails from forgeries. This highlights the need for a solution that mitigates human error, in addition to preventive measures and employee training, such as Whalebone Immunity.
Information is power, and unfortunately it is also easy to steal, trade and buy
According to Verizon, credentials (such as usernames and passwords) are the most compromised data in social engineering attacks, followed by internal data (such as sales figures) and personal data such as addresses and phone numbers. This underscores the need for organizations to implement robust security measures against social engineering attacks, such as advanced threat detection and response solutions like Whalebone Immunity.
Types of targeted information
Hackers can not only use stolen data, but often sell it on the dark web. Basically, for a few dollars, anyone can obtain a list of breached data and try to gain unauthorized access to company emails, internal databases and more. That’s why Immunity recently added identity protection to its feature set – Immunity catalogs all identified breaches associated with the customer’s domain over the past decade and alerts about new breaches.
Remote working offers significant benefits – for both employees and cybercriminals
A 2021 IRONSCALES survey found that 84% of IT professionals agree that remote working has made employees more susceptible to phishing attacks. This underscores the need for organizations to take measures to protect against phishing attacks not only within their internal networks, but also wherever their employees are working, whether on business trips, in cafes or from home offices.
Perceived impact of remote working on cyber attacks
Whalebone Immunity’s home office protection provides an effective way to extend your cyber security perimeter even beyond your corporate network. Make sure your employees are shielded at the DNS level, regardless of their location. Don’t let your network be compromised. In addition to preventive measures, there are risk mitigation strategies, such as Whalebone Immunity, that allow you to expand your cyber security perimeter. This prevents your employees from accessing malicious domains. However, this is just the beginning – contact our expert Adam Wright and request a free trial to eliminate vulnerabilities in your security framework.
Still have questions?
Contact [email protected] and we’ll be happy to help.



No Comments