
17 Aug Secure Your Network with Juniper Mist Access Assurance
In an era where connectivity is crucial, organizations need a robust network infrastructure to ensure secure and reliable access for users and devices. Juniper Networks, a leader in secure AI-driven networks, has developed a solution that addresses this need through its Juniper Mist Access Assurance service. This article will delve into what the Juniper Mist Access Assurance service is and how it is revolutionizing network access control.
What is Juniper Mist Access Assurance?
Juniper Mist Access Assurance is a cloud-hosted service that offers secure wired and wireless network access control based on user and device identities. It enforces zero-trust network access policies, ensuring that only authorized devices can connect to the network. This is particularly beneficial for handling guests, IoT, BYOD (Bring Your Own Device), and corporate devices.
The service extends the capabilities of Juniper Mist IoT Assurance by facilitating the onboarding of both headless IoT and BYOD devices and wired and wireless business devices. It employs 802.1X authentication or MAC Authentication Bypass (MAB) for clients not utilizing 802.1X.
Juniper Mist Access Assurance: Cloud-Based Network Access Control
Key Features of Juniper Mist Access Assurance
Client-First Experience
Access Assurance offers a holistic, unified view of the client connectivity experience, enabling IT teams to easily identify issues and perform root-cause analysis. By capturing all client events, including connection and authentication successes and failures, this service simplifies day-to-day operations and expedites the resolution of end-user connectivity issues.
Granular Identity Fingerprinting
One of the standout features of Access Assurance is granular identity fingerprinting based on X.509 certificate attributes. Additionally, the service utilizes intrusion detection and prevention information such as group membership, user account state, mobile device management (MDM) compliance state, client lists, and user location for more detailed fingerprinting.
Network Policy Enforcement
The service is capable of assigning users to specific roles and grouping them into network segments using VLAN or Group-Based Policy (GBP) technology based on user and device identity. This allows Access Assurance to enforce network policies associated with each segment.
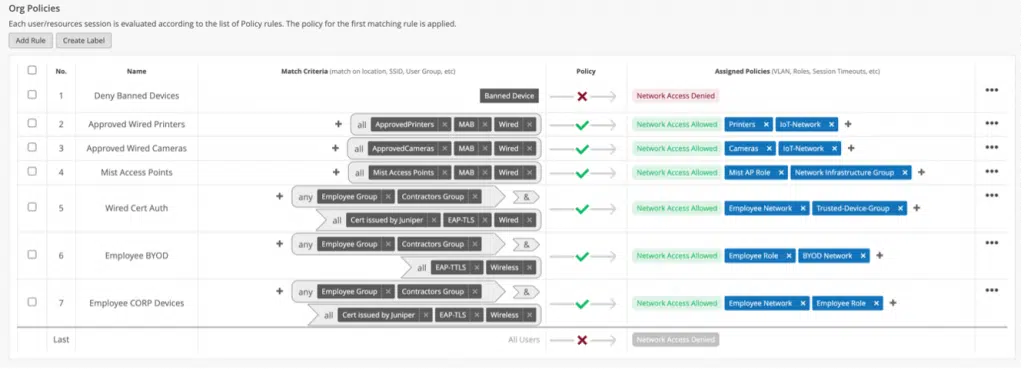
The flexible policy creation interface helps admins assign policies based on business requirements.
High Availability and Geo-Affinity
Organizations can rely on Access Assurance for low-latency network access control, regardless of whether they need to cover a single location or multiple sites. Thanks to Juniper’s deployment of cloud instances in multiple regional locations, authentication traffic is directed to the nearest instance, ensuring optimal response times.
Cloud-Native Platform
Access Assurance leverages the Juniper Mist cloud-native, full-stack network management platform, which eliminates the infrastructure requirements that are common with other network access solutions. This ensures consistent client experiences, irrespective of location.
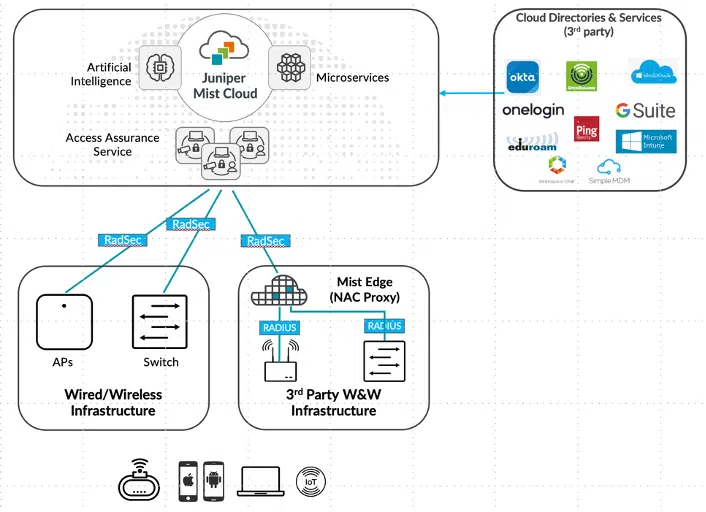
The Juniper Mist Cloud with Access Assurance Service.
Automatic Software Updates
Access Assurance stays optimized with the latest technologies through its microservices-based cloud architecture. New features, security patches, and updates are automatically added bi-weekly, without interruptions or service downtime.
External Directory Services Support
Access Assurance integrates with external directory services such as Google Workspace, Microsoft Azure Active Directory, Okta Workforce Identity, and others for authentication services. It also integrates with external Public Key Infrastructure (PKI) and MDM platforms.
100% Programmable APIs
The Juniper Mist platform is fully programmable, using open APIs for easy integration with external security information and event management (SIEM), IT service management, and other platforms for configuration and policy assignment.
Wrapping Up
Juniper Mist Access Assurance is a game-changer for organizations seeking to secure their network infrastructure. With its rich set of features including client-first experience, granular identity fingerprinting, network policy enforcement, and high availability, it addresses the complex challenges of modern network environments. By leveraging cloud-native capabilities and ensuring automatic updates, Access Assurance keeps your network secure, optimized, and future-proof.



No Comments