
15 Mar Privileged Access Management crucial for local government and healthcare sector
Although “privileged users” – internal and external administrators who perform maintenance on IT systems – are not mentioned as such, these types of users pose the greatest risks. Consider what would happen if their passwords fell into the hands of unauthorized people with the wrong intentions.
A good Privileged Access Management (PAM) solution is increasingly being considered to properly and quickly address these risks. A solution that ensures that access to business-critical applications and systems is properly managed.
An intuitive PAM solution consisting of Password Vault, Session Management and Session Analytics
One Identity offers a market-leading PAM solution, One Identity Safeguard. An intuitive PAM solution consisting of Password Vault, Session Management and Session Analytics. With standard use cases, we also guarantee short implementation times. With One Identity, you can make quick progress in setting up Privileged Access Management.
Privilege Access Management (PAM) is critical in healthcare for several reasons:
- Protecting sensitive data:
The healthcare industry deals with highly sensitive information, such as medical records and personal data of patients and clients. PAM helps manage and restrict access to this data, preventing unauthorized users from accessing confidential information.
- Regulation and compliance:
The healthcare industry must comply with strict regulations such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA). PAM helps organizations comply by managing access rights and reducing the risk of unauthorized access.
- Manage internal and external risks:
By implementing PAM, healthcare organizations can minimize the risk of internal threats, such as employee privilege abuse. It also helps reduce external risks, such as hacking and unauthorized external access, including controlled access for supply chain partners.
- Enhanced security:
PAM allows healthcare organizations to adopt a layered security approach by controlling access rights, preventing privilege escalation and monitoring for suspicious activity. This strengthens the overall security of systems/data.
Privilege Access Management (PAM) has a direct relationship with NEN7510 (a Dutch standard regulating the protection of information in healthcare), as PAM plays an important role in meeting the security requirements set forth in this standard. Some relevant aspects of PAM in relation to NEN7510 are:
– Access management: NEN7510 requires healthcare organizations to have strict controls in place to manage access to sensitive information.
– Monitoring and auditing: The standard emphasizes the importance of monitoring and recording access activities.
– Security measures: NEN7510 suggests security measures to protect sensitive information.
PAM plays an essential role in protecting sensitive information, complying with regulations and minimizing internal and external security risks in healthcare.
PAM is also the tool within healthcare to meet the specific information security and access control requirements of NEN7510. It enables healthcare organizations to better comply with the standard by adequately protecting sensitive data and systems.
Functioning of a PAM solution
With a PAM solution, administrators make the request to start a session. Once approved, they have access to perform maintenance for a specified period of time. Passwords are entered automatically and the entire session can be recorded and viewed. In case of suspicious activity, the analysis tool generates an alert so that action can be taken. For example, the session can be terminated immediately.
This prevents unauthorized access to applications and systems and unwanted actions during a maintenance session.
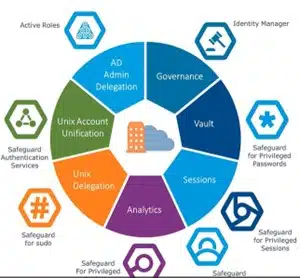
What is One Identity Safeguard?
Safeguard is an intuitive PAM solution that consists of Password Vault, Session Management and Session Analytics.
Key features:
– Discover: Quickly discover privileged accounts or systems on your network with host, directory and network search options.
– Secure: Authorized accounts are stored in a hardened physical or virtual appliance, increasing security and speeding installation and ongoing management.
– Capture: Capture all session activity, down to keystrokes, mouse movements and windows viewed.
– Monitoring: Traffic is monitored in real time, by humans or machines, so that appropriate actions can be taken automatically when certain actions appear on the command line or screen.
– Audit: All activity is captured, indexed and stored in encrypted, timestamped and cryptographically signed files for forensic and compliance purposes.
– Review: Activity can be viewed as video and searched as a database. Search for specific events in sessions and view the recording from the exact location where the event occurred.
– Analyze: Uncover previously unknown threats from inside and outside your organization using user behavior analysis technology.
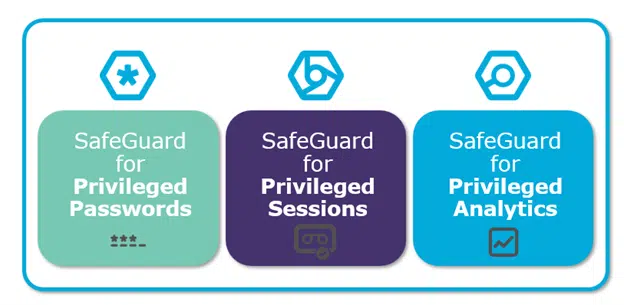
Safeguard for Privileged Passwords
Safeguard for Privileged Passwords automates, controls and secures the privileged credentialing process with role-based access management and automated workflows. The user-centric design of Safeguard for Privileged Passwords reduces the learning curve. It also allows you to manage passwords from any location, using almost any device. The result is a solution that protects your organization and gives your privileged users a new level of freedom and functionality.
Key features:
- Rapid asset detection and onboarding.
- Automated workflow engine
- Password approval from any location
- Full REST API
- Free personal password vault for business users
Safeguard for Privileged Sessions
Safeguard for Privileged Sessions lets you control, monitor and record privileged sessions of administrators, remote vendors and other high-risk users. The contents of recorded sessions are indexed for easy event search and automated reporting, so you can easily meet your audit and compliance requirements. In addition, Safeguard for Privileged Sessions acts as a proxy, inspecting application-level protocol traffic and denying traffic that violates the protocol, providing an effective shield against attacks.
Key features include:
- Full session auditing, recording and playback
- Real-time alerts and blocking
- Initiate workflows or deploy in transparent mode without changes for users
- Full text search with optical character recognition
Protection for privileged analytics
Protection for privileged analytics monitors questionable behavior and uncovers previously unknown threats from inside and outside your organization. Using user behavior analysis technology, Safeguard for Privileged Analytics detects anomalies and ranks them by risk, allowing you to prioritize and take appropriate action to ultimately prevent data breaches.
Key features include:
- Pattern-free analysis to detect unknown malicious behavior
- Full content analysis, including screen content, commands given and window titles
- Analysis of keystrokes and mouse movements to identify breaches
- Reduce alert noise by categorizing alerts by risk and anomaly level
InstantPAM
For local governments and other decentralized government agencies, we now also offer a combination of licenses and a basic implementation: InstantPAM.
This InstantPAM is set up by one of our certified partners, allowing you to get started with PAM even faster! Contact our sales at [email protected] for more information.



No Comments