
22 Aug Barracuda Networks API Discovery
The operating system makes a computer run, but it is the applications that do the actual work. Many of these applications rely on APIs: Application Programming Interfaces. What vital role do APIs play in our automated and interconnected world? Find out more in this blog post!
APIs are basically a gateway to all the important data stored by the application. They can be accessed internally, externally, or publicly and facilitate software development and innovation. They enable interactive websites such as comparison sites for booking travel, route apps that also show gas stations or speed cameras and, of course, important business SaaS applications such as customer relationship management apps that integrate with email. In short, APIs are great!
Welcome to the fantastic world of APIs! Oh, wait…
In an ideal world, every IT professional would know how to properly manage each API in their IT environment. In addition, they would know what data can be accessed through APIs, the commands that are enabled, which developers can access the APIs, and would be knowledgeable about security and authentication management to ensure that the APIs and the data behind them are secure.
Unfortunately, we don’t live in such an ideal world. Many companies have no idea what part of their IT infrastructure might be publishing data through APIs. IT environments are often a hotchpotch of legacy, on-premises and new, cloud-based systems, all functioning thanks to and held together by a web of internal and external applications. It is nearly impossible to get a clear view of these applications and their APIs. And what you can’t see, you can’t protect.

The API iceberg
There are three API categories, each with its own visibility and risk profile. The first category includes all visible, known APIs. These APIs may not be completely secure yet, but they are managed and secured to some degree. In addition, these APIs can be inspected and secured with security measures such as Web application firewalls and Zero Trust access because it is known where they reside.
The second category includes all “Shadow” APIs – APIs that you don’t know about because you don’t know that the applications in which they reside are part of the IT infrastructure. And the third and most risky APIs are the so-called “Zombie” or “Legacy” APIs. These can be found in older, inactive or deprecated applications. These APIs were probably activated when the application was first deployed and then were never closed or properly secured. Insecure or inadequate authentication measures can easily be abused by attackers to, for example, send commands to the application to siphon off data.
Misusing APIs
While more and more APIs continue to be added, Gartner expects less than 50% of all enterprise APIs to be managed by 2025. This also suggests that less than half of APIs will be known and secured. When you add to that the fact that APIs are a gateway to vast amounts of sensitive data and even to the network beyond, it is clear what a broad, unsecured attack surface APIs provide.
Recent examples of cyber attacks where unsecured APIs were abused and the data of millions of people were exposed include the T-mobile API hack (37 million customers affected), the Optus attack in Australia (up to 10 million customers affected) and the Twitter API security breach (data of more than five million users exposed).
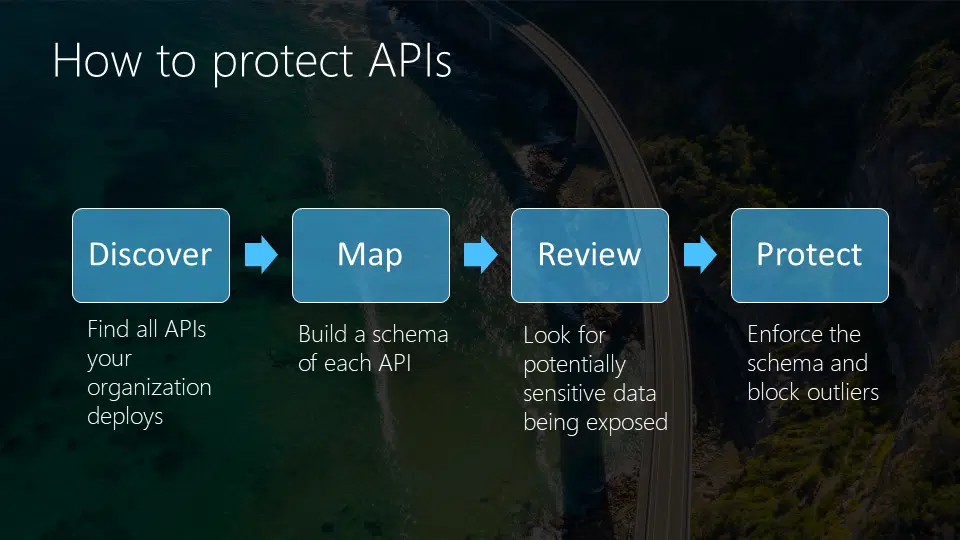
Finding APIs
Finding known and unknown APIs is difficult and time-consuming. Fortunately, there are solutions to make this faster and easier. For example, with a Web application firewall that inspects data traffic. This allows organizations to find hidden and unknown APIs by analyzing outgoing and incoming data traffic between applications “live. This uses machine learning to find known, partially known and unknown APIs. Companies can then decide how and which applications to secure and thus mitigate risk.
Securing APIs
The increasing number of APIs and their direct access to valuable data makes them an ideal target for attackers. This risk will only increase as more API-based applications are added. Barracuda research shows that just under two-thirds (63%) of IT professionals are concerned about security when setting up APIs. In addition, it shows that 44% are concerned because they do not know where all APIs are deployed or used. The most important step in securing API-based applications is visibility – of all APIs in the network and endpoints, regardless of whether they are internal or external, active or inactive. A Web application security solution with machine learning API detection is ideal for locating and securing Zombie and Shadow APIs.
In addition, complete visibility into all application traffic is a requirement. Log every request made to APIs. This allows you to quickly detect suspicious commands or patterns in data traffic and troubleshoot problems, such as a denial-of-service (DoS) attack or attackers trying to send a “download all data” command. Set up robust access controls for API-based applications to restrict API access to authorized users. And finally, integrate security tools into the application software development cycle as early as possible.
Do you have questions? Feel free to contact us at [email protected]!



No Comments